

|
Red-Database-Security GmbH is specialized in Oracle SecurityProductsRepscan 2.5 Hedgehog Enterprise Checkpwd (free)
Services
Information
Company |
Read File via iSQL*Plus load.uix
Details Read any file on the server. Every database user can exploit this vulnerability and read files, e.g. with cleartext passwords. Example 1. Login to iSQLPlus (e.g. scott/tiger) 2. http://server:5560/isqlplus/load.uix 3. Enter an absolute path in the FILE input box. 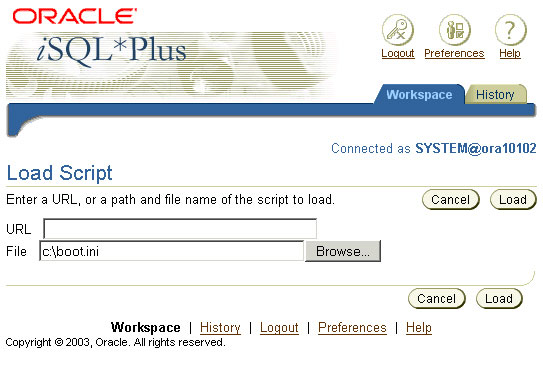
Patch Information Apply Oracle patch 68 or later (e.g. Critical Patch Update October 2005). © 2005 by Red-Database-Security GmbH - last update 02-nov-2005 |
Hardening Oracle Application Server
|